estimateNetworkOutputBounds
Syntax
Description
[
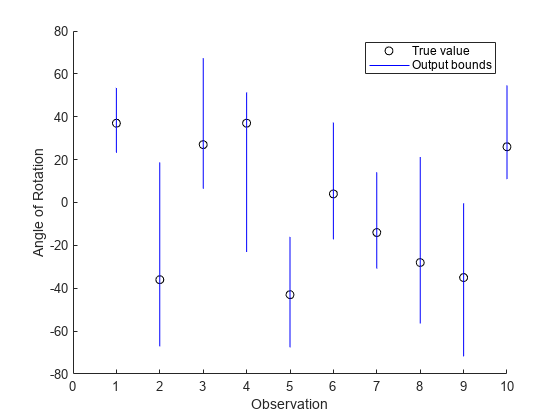
estimates the lower and upper output bounds, YLower,YUpper] = estimateNetworkOutputBounds(net,XLower,XUpper)YLower and
YUpper, respectively, of the network net for input
within the bounds specified by XLower and XUpper.
The function estimates the range of output values that the network returns when the input is between the specified lower and upper bounds. Use this function to estimate how sensitive the network predictions are to input perturbation.
The estimateNetworkOutputBounds function requires the Deep Learning Toolbox Verification Library support package. If this support package is not installed, use the
Add-On Explorer. To open the Add-On Explorer, go
to the MATLAB® Toolstrip and click Add-Ons > Get Add-Ons.
[
estimates the lower and upper output bounds with additional options specified by one or more
name-value arguments.YLower,YUpper] = estimateNetworkOutputBounds(___,Name=Value)
Examples
Input Arguments
Name-Value Arguments
Output Arguments
Algorithms
Let X be the input for which you want to estimate the output bounds. To
use the estimateNetworkOutputBounds function, you must specify a lower
and upper bound for the input. For example, let be a small perturbation. You can define a lower and upper bound for the input
as and , respectively.
To estimate the output bounds for the network net and the input bounds
Xlower and
Xupper, the function performs these steps.
Create an input set using the lower and upper input bounds.
Pass the input set through the network and return an output set. To reduce computational overhead, the function performs abstract interpretation by approximating the output of each layer using the DeepPoly [2] method.
Return the minimum and maximum estimated output values for the input set.
If you specify multiple pairs of input lower and upper bounds, then the function estimates the output bounds for each pair of input bounds.
Note
Soundness with respect to floating point: In rare cases, floating-point rounding errors can accumulate which can cause the network output to be outside the computed bounds and the verification results to be different. This can also be true when working with networks you produced using C/C++ code generation.
References
[1] Goodfellow, Ian J., Jonathon Shlens, and Christian Szegedy. “Explaining and Harnessing Adversarial Examples.” Preprint, submitted March 20, 2015. https://arxiv.org/abs/1412.6572.
[2] Singh, Gagandeep, Timon Gehr, Markus Püschel, and Martin Vechev. “An Abstract Domain for Certifying Neural Networks”. Proceedings of the ACM on Programming Languages 3, no. POPL (January 2, 2019): 1–30. https://doi.org/10.1145/3290354.